A Guide to Terraform Audit Logs
Why are Terraform audit logs essential? What should they contain? How can they help with monitoring and workflow automation?
For any organization using Infrastructure as Code (IaC), maintaining a clear record of changes is not just a best practice; it is a necessity for security and governance. Terraform audit logs provide this crucial, immutable record, detailing every action taken that affects your infrastructure. Effectively managing and utilizing these logs is fundamental to a secure, compliant, and operationally sound Terraform practice.
This guide explains why Terraform audit logs are essential, what information they should contain, and how you can leverage them for centralized monitoring and to power event-driven workflows.
Why Your Organization Needs Terraform Audit Logs
A complete audit trail answers the critical questions of who, what, and when for every change. Without a robust system for Terraform audit logs, organizations are exposed to significant security, compliance, and operational risks.
Security and Incident Response
In the event of a security incident, Terraform audit logs are your primary source of truth. They provide a detailed timeline of events, enabling security teams to trace the origin of a breach, understand the scope of unauthorized changes, and identify the responsible party. For example, if a sensitive variable is accessed or a security group is modified, the audit log will show precisely which user or service account initiated the action, from what IP address, and at what time.
Meeting Compliance Requirements
Many regulatory frameworks like SOC 2, HIPAA, and PCI DSS have strict requirements for logging and auditing. To pass an audit, you must be able to prove that all changes to your infrastructure are tracked and authorized. Terraform audit logs serve as the definitive evidence to satisfy auditors and demonstrate that you have control over your production environment.
Operational Stability and Troubleshooting
When a deployment fails or an application experiences an outage, the first question engineers ask is, "What changed?" Terraform audit logs provide a clear history of all recent activities, allowing teams to quickly correlate a change with a problem. This significantly reduces mean time to resolution (MTTR) and helps prevent similar issues in the future by understanding the root cause.
What to Capture in Terraform Audit Logs
A useful audit logging system for Terraform must capture more than just run events. To provide complete visibility, your Terraform audit logs should include a wide range of activities across the platform. Key events to capture include:
- User and Authentication Events: Logins, logouts, and failed authentication attempts.
- Administrative Changes: Modifications to workspaces, environments, user permissions, and VCS provider settings.
- Variable and State Access: Creation, updates, and deletions of variables (especially those marked as sensitive).
- Run Lifecycle Events: Run creations, approvals, denials, and cancellations.
- Object Creation/Deletion: Events for when workspaces, environments, or other resources are created or deleted.
Each log entry must contain sufficient context, including a timestamp, the user who performed the action, their source IP address, and a detailed message describing the event.
How Scalr Provides Comprehensive Terraform Audit Logs
While Terraform itself performs actions, it doesn't inherently provide a centralized, persistent audit logging system that captures the full spectrum of user and administrative activities. This is where a platform like Scalr becomes essential. Scalr is designed with auditing at its core, capturing every event that occurs within the platform.
Scalr automatically generates detailed audit logs for all the critical events, from user logins to variable creation and run approvals. These logs are easily streamed to external logging platforms for administrators and security teams to consume easily. This built-in capability ensures that you have a complete Terraform audit log without requiring complex manual setup.
Centralizing Terraform Audit Logs
For enterprise-wide security monitoring and operational visibility, Terraform audit logs must be integrated with your existing observability and event management platforms. Centralizing these logs allows your teams to correlate infrastructure changes with events from other systems and apply their established monitoring, dashboarding, and alerting rules.
Scalr provides direct integrations to stream audit logs and events to leading cloud platforms.
Demo of audit logs for Terraform
Sending Audit Logs and Events to Datadog
Scalr can send audit logs directly to Datadog Logs. This allows you to unify your Terraform audit logs with application, security, and other infrastructure logs already being collected in Datadog. Once in Datadog, you can use its powerful search, analytics, and visualization features to create dashboards that track key Terraform activities, monitor for specific security events, and set up alerts on suspicious behavior.
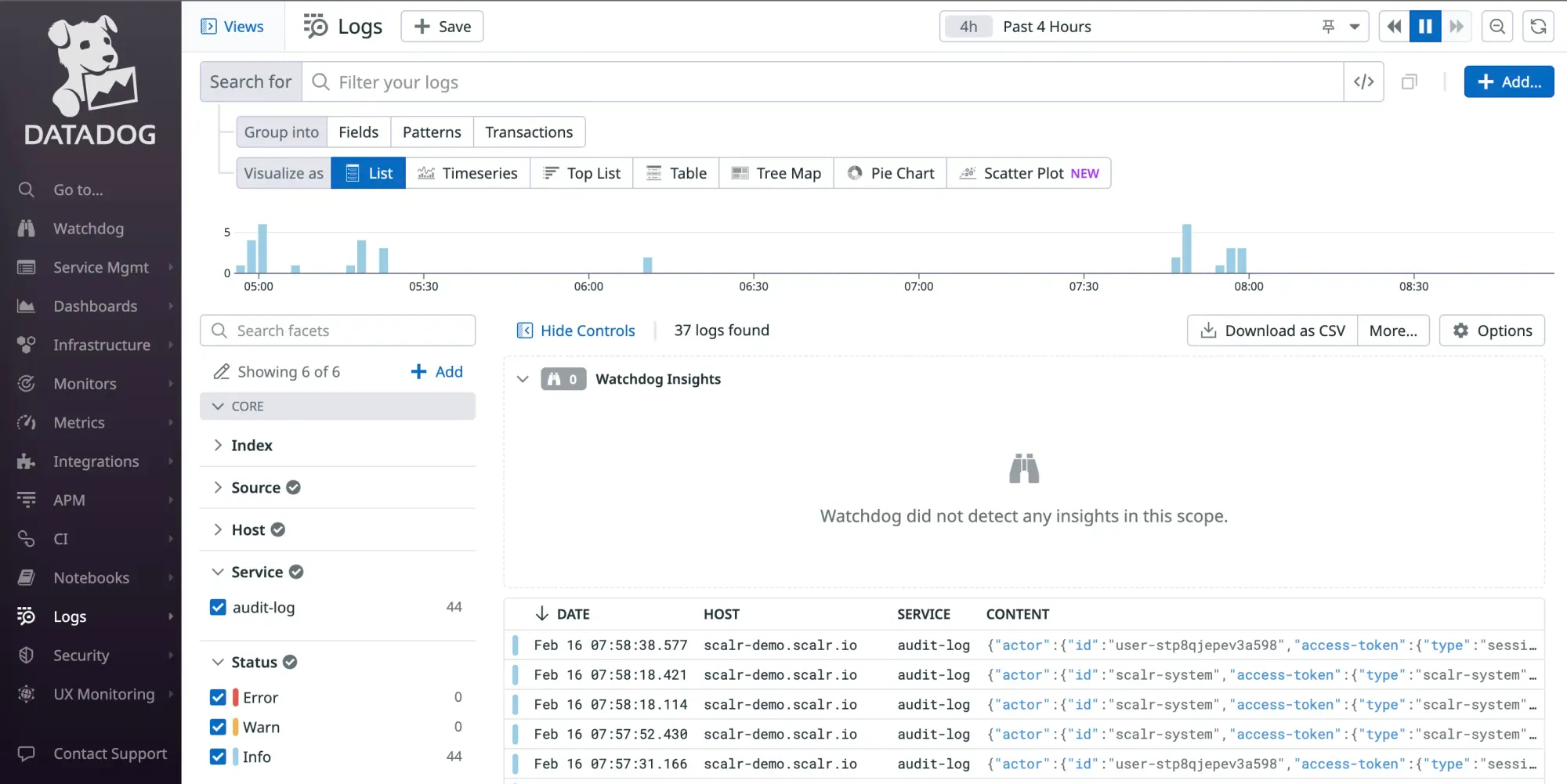
Scalr also sends events to Datadog, such as when a run errored, how the run was executed, and when. While these details are similar to audit logging, they can also be used for monitoring and alerting in event-driven workflows, as seen below.
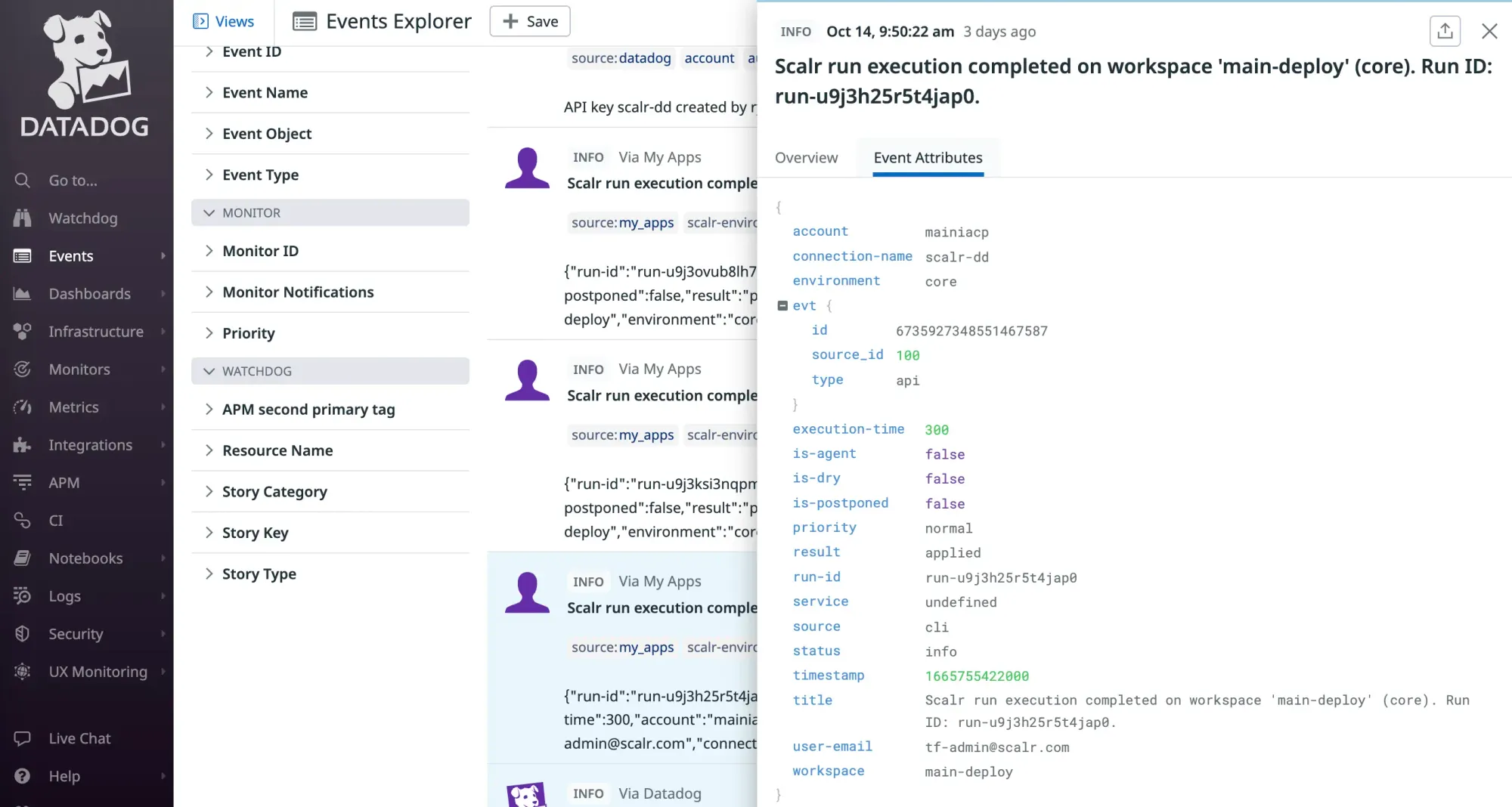
See the official docs on how to set up the integration with Datadog here.
Sending Audit Logs and Events to AWS Eventbridge
Scalr also sends the same audit log details to AWS Eventbridge. This integration gives users the flexibility of forwarding it to any third-party tool that Eventbridge integrates with or to another service in AWS, such as CloudWatch.
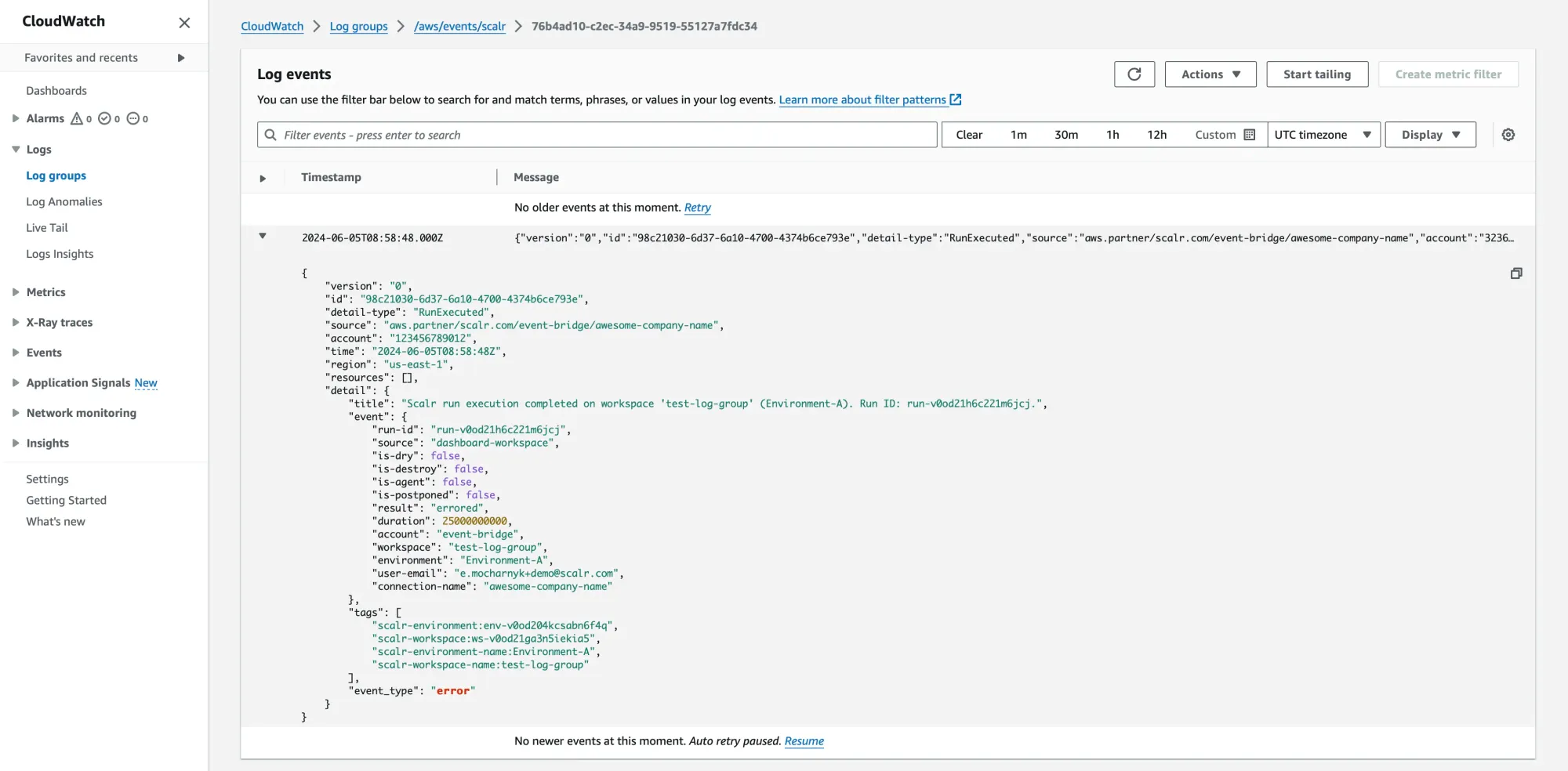
For more than just logging, Scalr also send events directly to an Amazon EventBridge event bus. This integration is designed for action, turning an event into a trigger. Scalr sends a structured JSON payload for events like run.completed, run.needs_attention, and workspace.created, which can then be used to invoke a wide range of AWS services.
See the official docs for the Scalr integration with AWS Eventbridge here.
Using Terraform Audit Logs for Event-Driven Workflows
The real power of modern audit logging comes from using events to drive automated workflows. By streaming events from Scalr to AWS EventBridge, you can move beyond passive monitoring and build active, automated systems that respond to infrastructure changes in real time.
When Scalr sends an event to your EventBridge event bus, you can create rules that filter for specific events and route them to targets. This enables powerful automation, such as:
- Triggering an AWS Lambda function when a
run.completedevent occurs for a production environment. The function could create a change ticket in Jira, post a custom summary to a Slack channel, or run a post-deployment validation script. - Starting an AWS Step Functions workflow when a
workspace.createdevent is detected. This could orchestrate a series of compliance checks, apply a standard set of policies, and notify a platform administrator that a new workspace is ready for review. - Sending a notification via Amazon SNS when a
run.erroredevent happens. This can be used for customized email, SMS, or PagerDuty alerts that go beyond standard notifications.
By connecting the detailed events from your Terraform audit logs to a service like AWS EventBridge, your organization can build a responsive, automated, and secure infrastructure management practice.

