Explaining a Terraform Private Module Registry
A Terraform Private Module registry: the secure, internal source of truth for all your organization specific Terraform configurations
Introduction
If your organization relies on Terraform or OpenTofu to manage infrastructure at scale, you’ve likely run into a common set of challenges: code inconsistency, security gaps, and teams spending too much time reinventing the wheel. While the public Terraform Registry is invaluable for third-party providers, relying on it, or worse, pointing configurations directly to specific Git repository branches, leaves your internal code susceptible to inconsistency and poor governance.
The solution is a Terraform Private Module Registry. This central service acts as the secure, internal source of truth for all your pre-vetted, organization-specific Terraform configurations. This post will explore why the private module registry is essential, how it works, and how you can implement it to immediately boost your infrastructure efficiency, security, and standardization.
What is a Terraform Private Module Registry?
A Private Module Registry is an organization-owned, centralized repository dedicated to storing, sharing, and managing Terraform modules.
It is distinct from the Public Registry in its purpose and audience:
Feature | Public Registry | Private Module Registry |
|---|---|---|
Audience | Global community, public consumption | Internal organization, restricted access |
Content | Third-party providers, generic modules | Proprietary, hardened, internal modules |
Governance | Community/HashiCorp Vetting | Organization enforced security & compliance |
The primary artifact stored in this registry is a Private Module. These are the reusable configurations built by your Platform or DevOps teams, such as a "Standard VPC with enforced tagging" or a "Hardened RDS Database instance" that automatically applies corporate compliance rules.
The Core Benefits of Going Private
A private registry moves module management from an ad hoc process to a centralized platform engineering function, yielding five major benefits:
1. Enhanced Security & Compliance
The private module registry enables the "golden image" approach. Platform teams can vet a module for security and compliance once. Once approved and published, application teams consume this pre-hardened infrastructure, ensuring security standards are met by default. Proprietary intellectual property or complex, sensitive configuration logic remains safely inside the corporate boundary, never exposed to the public internet.
2. Standardization and Consistency (The "Golden Path")
Configuration drift is the enemy of stability. By forcing teams to use the same module for core infrastructure, like networking or IAM roles, you guarantee consistency across all environments and projects. This standardization simplifies operations, reduces debugging time, and makes auditing significantly easier.
3. Improved Developer Experience and Discoverability
Imagine an "App Store" for infrastructure. The private module registry provides a single, searchable catalog where engineers can browse, filter, and discover pre-vetted components. Since registries typically auto-generate documentation from your module's README.md, developers spend less time hunting down the right code and more time building features.
4. Simplified Dependency Management
Directly pointing to Git repositories often requires pinning to a specific commit SHA, making upgrades difficult. The registry leverages the full power of Semantic Versioning (SemVer). Module consumers can use intelligent version constraints (e.g., version = "~> 1.2.0") to automatically pull in bug fixes without risking breaking changes, drastically reducing maintenance burden.
5. Decoupling Consumer from Source
When consuming a module via Git, the consumer’s code is tightly coupled to the repository location. If you need to move the module repository, every consuming configuration breaks. By using the private module registry, consumers reference a logical name (e.g., account.scalr.io/org/vpc/aws). The registry acts as an abstraction layer, meaning you can reorganize your backend storage without changing thousands of consuming configurations.
How to Set Up a Private Module Registry
The two primary methods for establishing a private module registry are managed solutions and self-hosted options.
Option 1: Managed Solution (Recommended for Enterprise)
The most popular and easiest path involves using platforms that offer built-in private registry capabilities. These solutions provide native VCS integration and handle the complex API protocol required by Terraform, minimizing operational overhead. Key native options include:
- Scalr: A comprehensive Infrastructure as Code management platform that includes a fully featured private registry. It automatically syncs private modules from your VCS (GitHub, GitLab, etc.) when your Platform team tags a release with SemVer (e.g.,
v1.2.3). Scalr allows for extensive customization, policy enforcement (OPA/Sentinel), and self-service provisioning. The registry is included on the free tier, Scalr supports Terraform or OpenTofu. - Terraform Cloud / HCP Terraform: It automatically syncs private modules from your VCS (GitHub, GitLab, etc.) when your Platform team tags a release with SemVer (e.g.,
v1.2.3). It offers zero infrastructure to manage and integrates seamlessly with role-based access control and workspace execution. This is included on their free tier, only Terraform is supported. - GitLab: For organizations already using GitLab for their VCS and CI/CD pipelines, GitLab provides a built-in, native Terraform Module Registry. This is highly convenient as it keeps the source code, pipelines, and the registry all within the same platform, streamlining the release and discovery process without needing a third-party tool. Gitlab is not purposefully built for Terraform, like Scalr and Terraform Cloud.
Regardless of the platform chosen, the main benefit is zero infrastructure management, native VCS integration, and centralized authentication and access control.
Option 2: Self-Hosted/Open Source (For Custom Needs)
For organizations with strict air-gapped requirements or specific compliance needs, self-hosted options are available. These tools, such as Terrakube or others that implement the Terraform Module Registry Protocol , require setting up and maintaining the API endpoints and underlying module storage yourself. This method provides maximum control but comes with significantly higher operational overhead.
Using a Private Module (Code Example)
The best part of using a private module registry is the clean, readable syntax it provides.
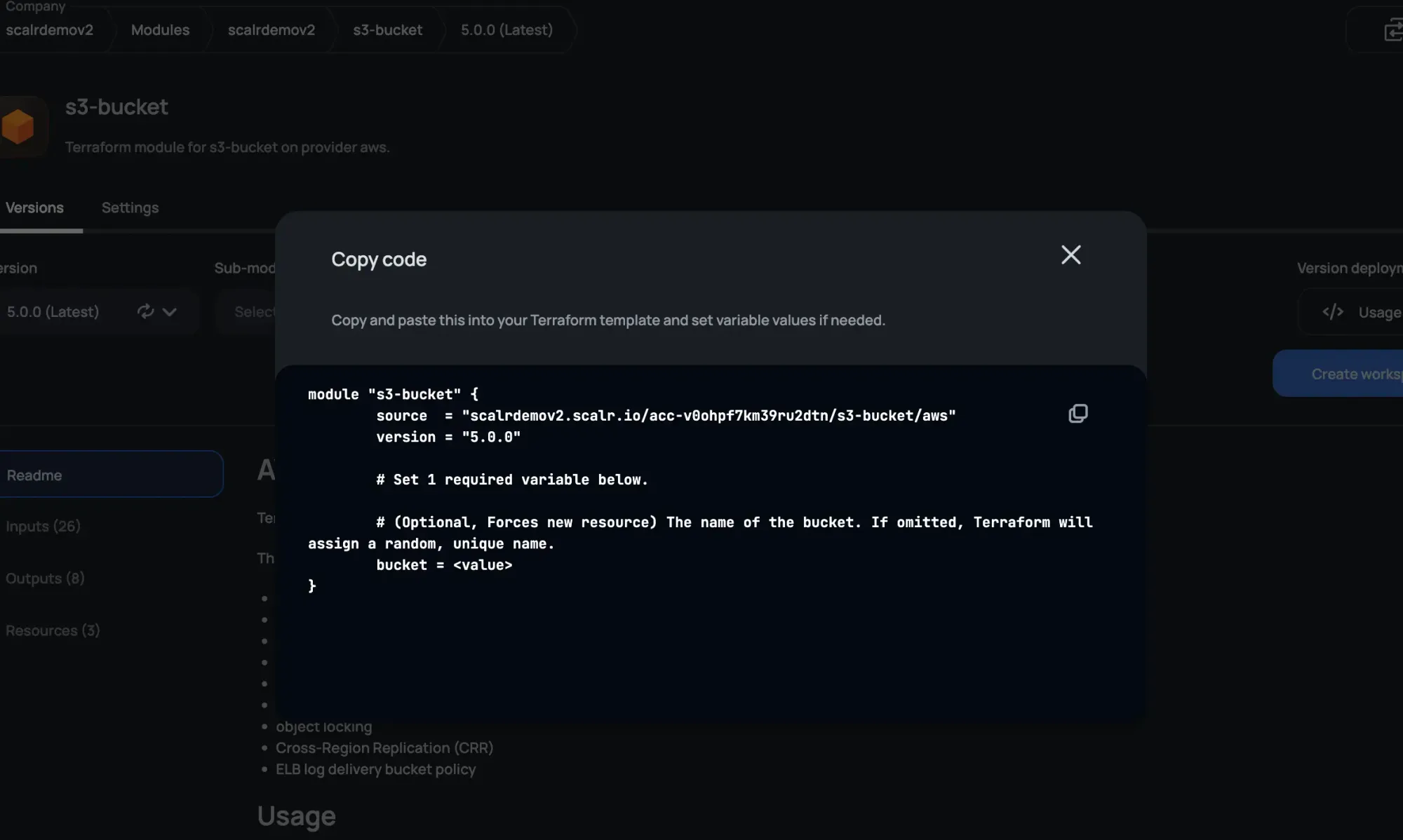
Note the difference between sourcing a public module and a private one through HCP Terraform:
Public Registry Example:
module "vpc" {
source = "terraform-aws-modules/vpc/aws"
version = "5.0.0"
# ... variables
}
Private Registry Example (Scalr):
module "standard_vpc" {
source = "<account>.scalr.io/<ACCOUNT_NAME>/standard-vpc/aws"
version = "1.2.3"
# ... variables
}
Notice the source clearly points to your organization's hostname and namespace, making it immediately clear this is an internal artifact. Authentication is seamlessly handled via the terraform login command or API tokens configured in your CLI, removing the need for developers to manage granular VCS credentials.
Best Practices for Private Module Registry Management
To maximize the value of your private module registry, adhere to these best practices:
- Mandate SemVer: Enforce strict adherence to Semantic Versioning (
MAJOR.MINOR.PATCH). A change that breaks compatibility must result in a major version bump. - CI/CD Integration is Non-Negotiable: Every module change must undergo automated testing (
terraform testand static analysis) before it is tagged and released to the registry. The registry acts as the final gate. - Implement Producer/Consumer Access Control: Clearly define which Platform Engineering teams have the permission to publish modules and which application teams only have permission to consume them.
- Prioritize Documentation: A module is only as good as its documentation. Ensure every module's repository contains a high-quality
README.mdto feed the registry’s auto-generated documentation feature.
Conclusion
A Terraform Private Module Registry transforms your IaC workflow from a series of disjointed repository calls into a unified, high-assurance service. By centralizing your modules, you achieve unparalleled scale, enforce enterprise security standards by default, and dramatically improve the efficiency of every engineer in your organization. If you’re serious about adopting platform engineering principles, migrating your critical, proprietary, and hardened modules to a private module registry is the essential next step.
Try out Scalr's private module registry for free!

