Scalr Product Updates - July 2025
Terraform module namespaces, AWS provider default tags, and more!
Features
Module Registry Namespaces
The Scalr UI now supports custom namespaces for module publishing and management, allowing users to create, view, update, and organize modules under custom account-level namespaces. Previously, a module could only be created at the account scope or within an environment. Now, a namespace can only be created at the account scope. The namespace owner can choose if the modules in the namespace can be shared with all environments or select specific environments to share them with.
All existing module URLs remain fully functional after the migration to namespaces — any existing module calls using the previous account or environment scope will continue to work without changes.
See the full docs here.
Support for Apply Before Merge in Gitlab
Scalr now supports Atlantis-style workflows in GitLab, allowing you to trigger Terraform plan and apply operations directly from pull request comments using commands like /scalr plan, /scalr apply, /scalr approve, and /scalr decline. This feature integrates seamlessly with your existing GitLab merge request workflow and provides automated status feedback directly in PR comments.
AWS Provider Default Tags
Scalr now supports setting default tags at the AWS provider configuration level. These tags automatically apply to all AWS resources created through Terraform using that provider configuration. This ensures consistent tagging across your infrastructure without manual intervention and reduces operational overhead by eliminating repetitive tag definitions.
Configure key-value tag pairs in your AWS provider configuration settings. Select a merge strategy (skip or update) to define how conflicts between provider-level and resource-level tags should be handled.
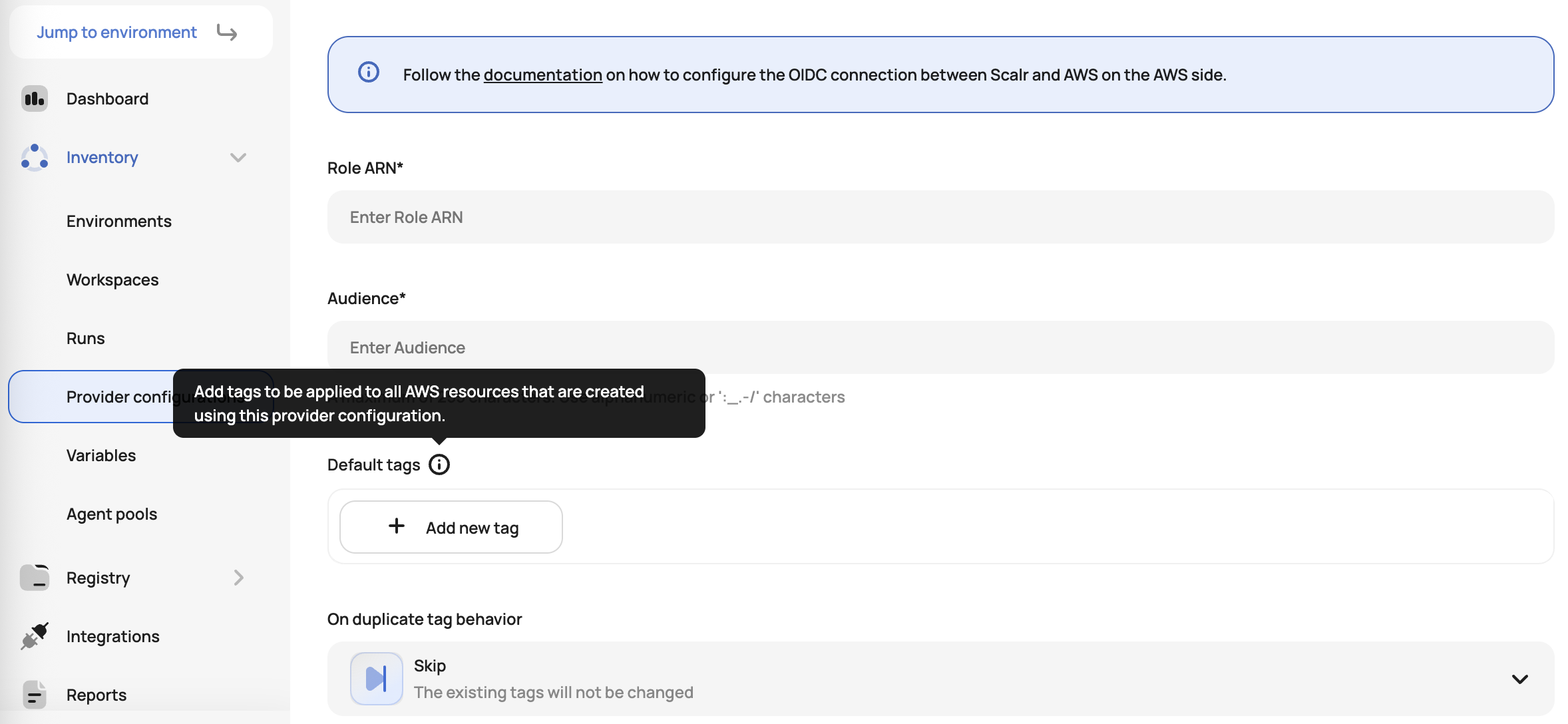
Note that agent version 0.50.0 or higher is required for runs using an agent. The provider update for this will be released on July 11th, 2025. See the docs on this here.
Enable GitHub Checks
Scalr now integrates with GitHub checks by sending run results directly back to the checks. This allows for the full run output to be sent back into GitHub, rather than just a summary.
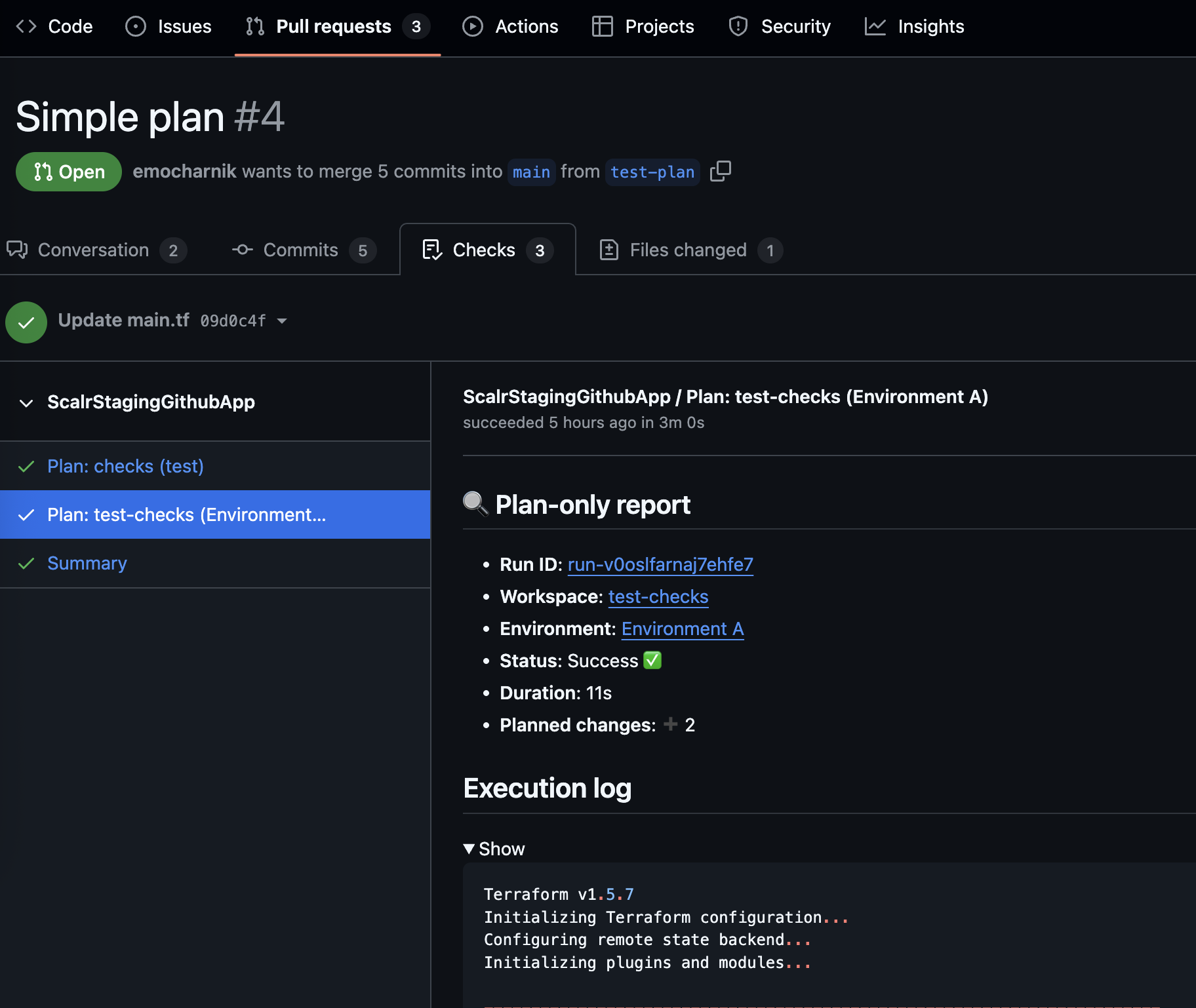
Each new commit will trigger fresh checks, while manual commands (/scalr plan) will replace existing individual checks based on the same commit. There are no changes to existing workflows - this is an opt-in feature that enhances GitHub integration without affecting current operations. See the docs on this here.
Assign Agent Pools to Environments
Scalr now supports restricting which environments can access specific agent pools (Runs type only). Account admins can control agent pool usage and enforce the assignment of pools to environments.
No changes are required for existing agent pools; they remain shared with all environments by default. You can implement access restrictions gradually based on your security and organizational requirements.
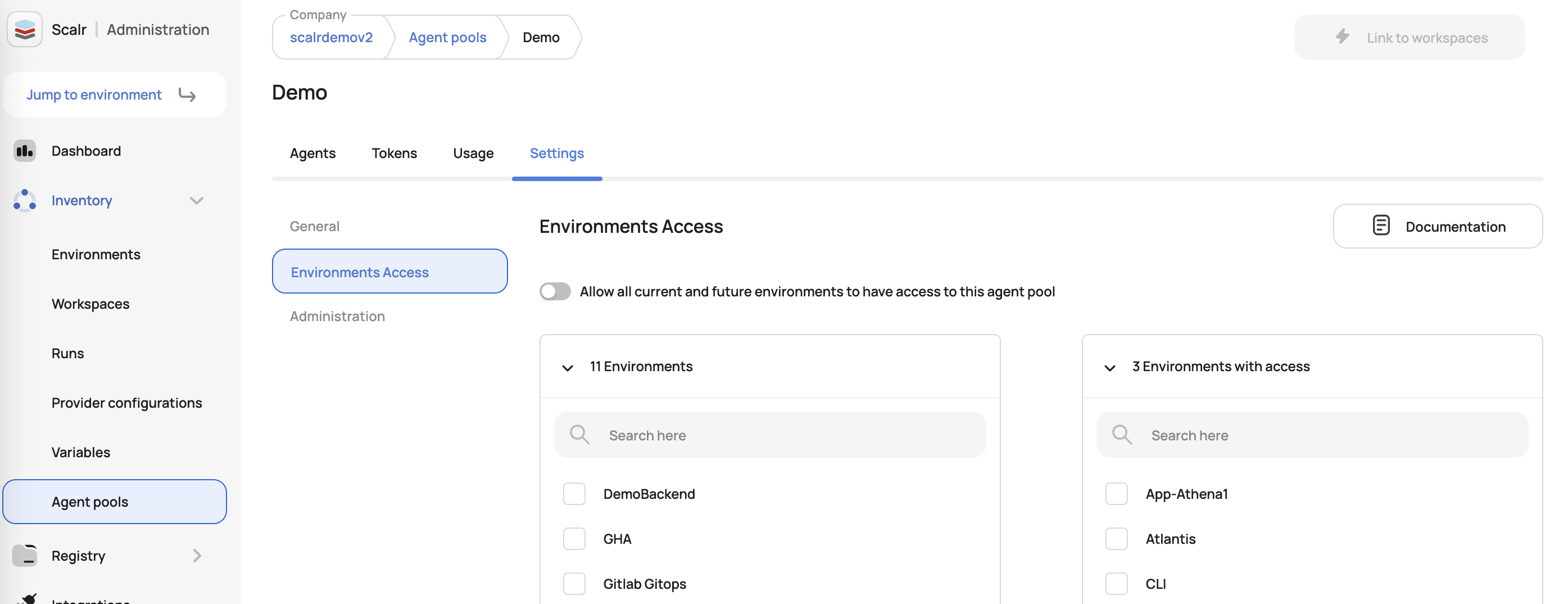
This feature enhances security by preventing unauthorized cross-environment access to agent pool and improves compliance and governance through controlled access to infrastructure resources. See the docs on this here.
Improvements
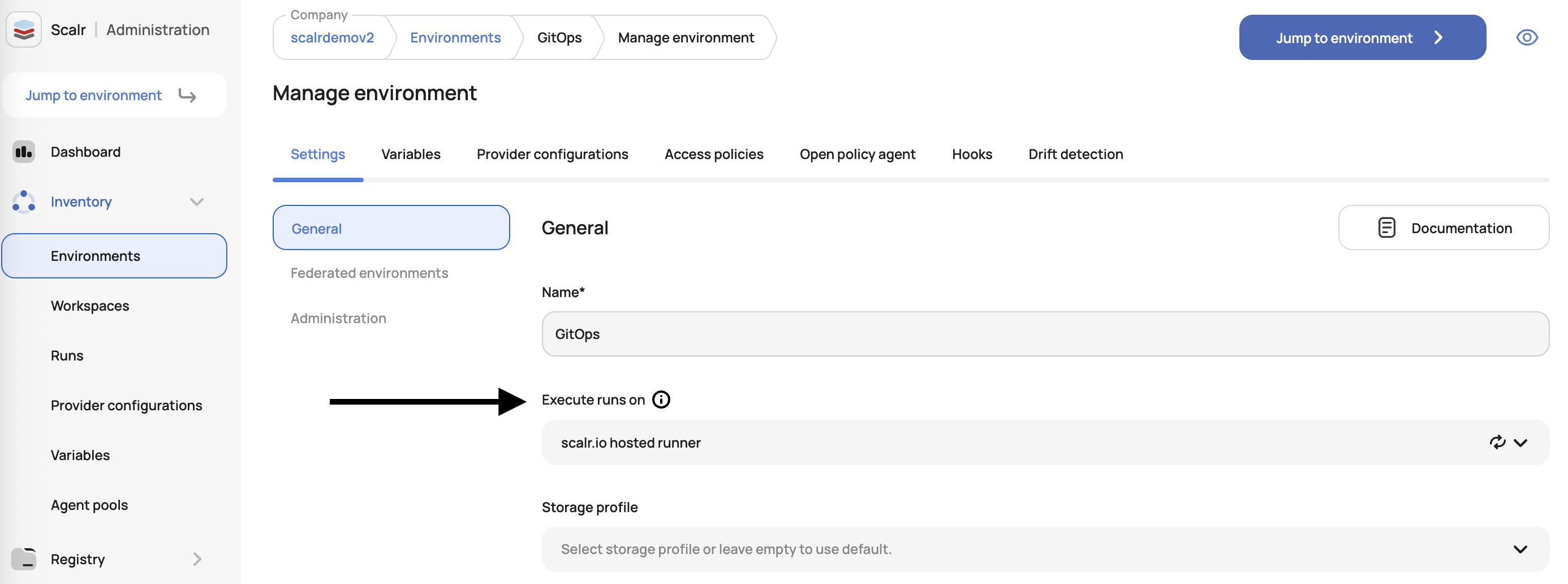
Default Agent Pools for Environments
Environment admins can now set a default agent pool at the environment level. New workspaces in that environment will automatically inherit this pool, reducing manual setup. Workspace owners can choose to override the agent setting within the workspace.
HCL Support in Custom Provider Configurations
Scalr now supports an hcl flag that enables users to define complex HCL-style values like maps and nested structures directly within custom provider configuration parameters via the API. The flag can be added to parameters for both new and migrated custom provider configurations through public endpoints.
Azure DevOps Integration Updated:
Added Personal Access Token and Microsoft Entra ID authentication options to replace the deprecated OAuth2 flow that Microsoft no longer supports. Existing OAuth integrations continue working without changes, while new connections can choose between "Custom Azure Application" (using App ID, Tenant ID, and Client Secret) or "Personal Access Token" (requiring Code Read/Status and Pull Request permissions). Follow the updated docs when creating new Azure DevOps connections.
Expiration Date Added to API Tokens Report
Added expiration date display and status filtering to help you easily manage token lifecycle and bulk remove expired tokens.
Improved Sorting in IAM - Roles Table
Default sorting in IAM > Roles table is now by name instead of ID, making it easier to find entries without manual sorting.
OpenTofu State Files Now Formatted
Scalr now displays OpenTofu state files in a clear, beautified, and scrollable format within the dashboard, making it easier to navigate and extract information from large state files without dealing with unformatted or hard-to-read outputs. The improved state file viewer is automatically available for OpenTofu workspaces with no action required, while existing Terraform workspace views remain unchanged.
Run Level Variables
Scalr now supports defining temporary variables that apply only to a single Terraform or OpenTofu run through the Terraform/Tofu CLI, Scalr API, or Scalr CLI. This eliminates the need to modify persistent workspace, environment, or account-level configurations for one-off changes. Use the POST create_run API endpoint to define these run-specific variables, with no changes required to existing setups.
Example: terraform plan -var="subnet_name=public"
Run Mode Now Sent to Slack Notifications
Slack notifications for runs now include a "Run mode" section that clearly indicates whether the run is Plan only, Plan & Apply, Refresh only, Skip refresh, Replace, or Destroy. This eliminates the need to switch between Slack and Scalr to understand what type of run was triggered, helping you make faster decisions about whether to ignore the notification or take immediate action. No changes are needed; all new Slack notifications will now include this information.
Tags and VCS Data Now in Webhook Payloads
The data sent to webhooks now includes tags and VCS (repository, branch, commit) data in webhook event payloads. No changes are required for your current workflows. Existing webhooks will continue to function, but now provide additional data for enhanced filtering and automation.
Reports are Now Available for Non-Scalr Backends
The Scalr backend is optional, but previously when disabled, users had limitations in viewing reports. That limitation is now removed as Scalr will display reports for modules, providers, resources, and stale workspaces for environments and workspaces that have the remote backend disabled. Runs on agents are not supported yet, but will be added soon.
Terragrunt Support for "skip" and "exclude" Flags
Scalr now supports Terragrunt's skip and exclude flags in Terragrunt-based workspaces, enabling modules to be conditionally excluded from runs without causing failures. This update resolves the previous requirement for every module to produce a planfile, which caused runs to fail when valid Terragrunt skip logic was used. Existing setups will benefit from improved reliability when using skip or exclude rules, while workspaces without these flags remain unaffected.
Enhanced Checkov Integration Output Options
The Checkov integration now supports structured output formats, including JSON, alongside the standard CLI output. Users can switch between output types, search and filter results, and download reports directly from the Scalr interface.
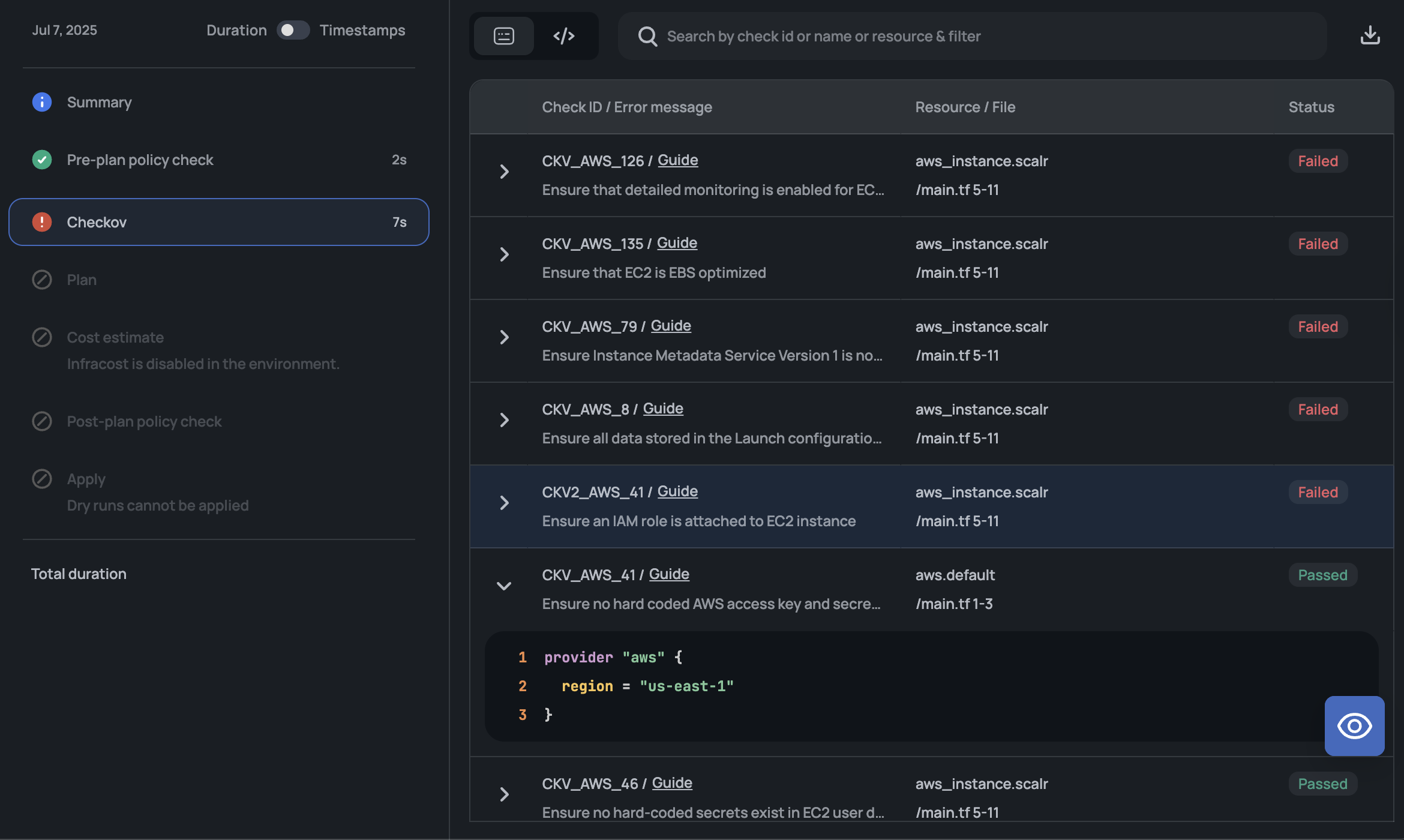
Select your preferred output type (Log or JSON) in the Scalr UI on the Run dashboard, then download results as needed.
Improved GitHub PR Mergeability Handling
Scalr now retries fetching PR mergeability status from GitHub when the value is unknown (up to 3 attempts) and provides clear, mapped error messages based on GitHub's mergeable_state responses. Previously, the value "unknown" would be returned, which was not helpful.

