Scalr Security Features for Terraform and OpenTofu
Learn how Scalr secures Terraform & OpenTofu with fine-grained RBAC, SSO, OPA policy-as-code, secret isolation, SOC 2 compliance and full audit trails.
SSO & Identity Management
Scalr incorporates several features for managing user identities and access within a TACOS environment:
SAML 2.0 Support: Scalr supports SAML 2.0, enabling integration with existing corporate identity providers (IdPs) for Single Sign-On (SSO). This allows users to authenticate using their standard organizational credentials.
SCIM Protocol Support: The SCIM (System for Cross-domain Identity Management) protocol is supported for automated user provisioning and de-provisioning. This synchronizes user access to Scalr with changes in the organization's identity system.
OIDC for Scalr API: Scalr supports OpenID Connect (OIDC) for authentication to the Scalr API, providing a token-based mechanism for programmatic access.
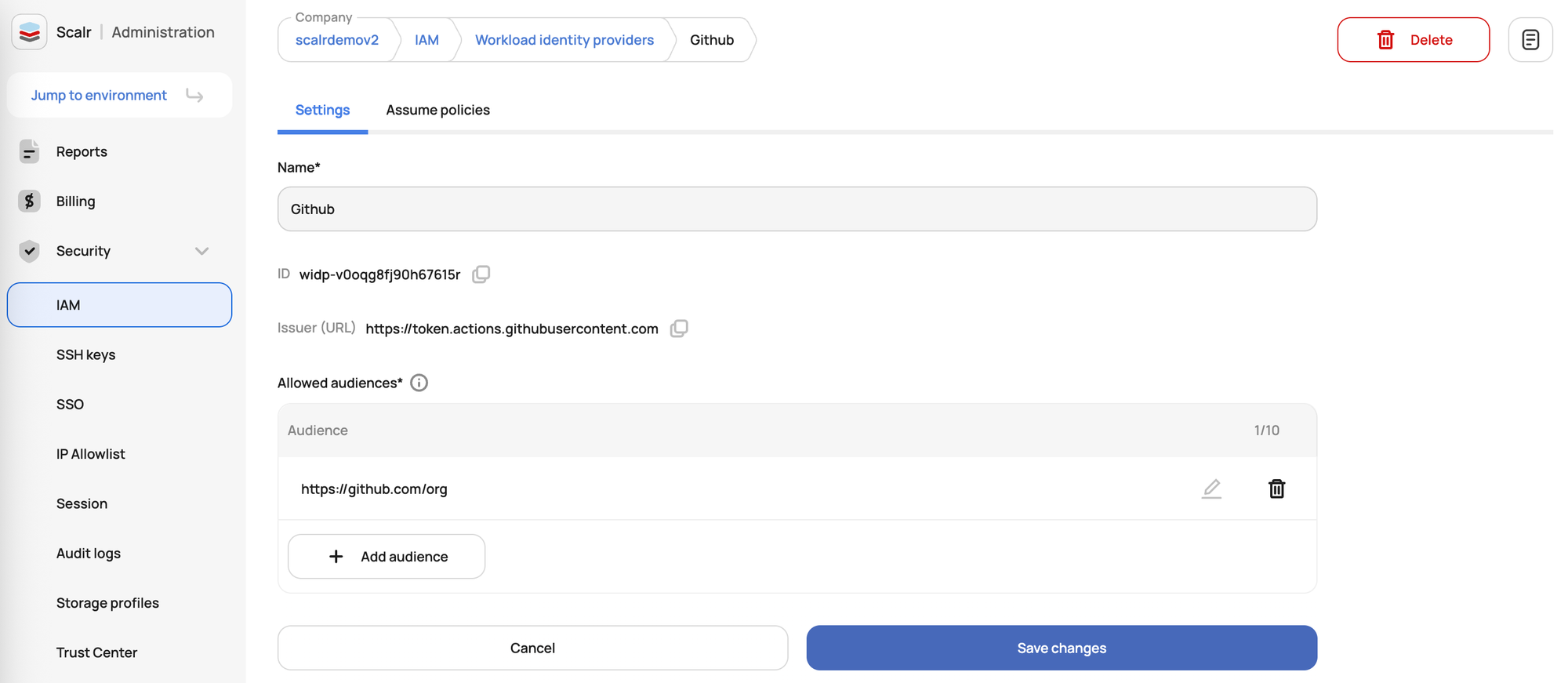
Cloud Credential Management
Scalr includes a feature for managing credentials used to interact with cloud service providers:
Provider Configurations: Scalr provider configurations are how you securely store and manage the credentials Scalr needs to authenticate with your cloud platforms (like AWS, Azure, GCP) or other services that Terraform interacts with. These centrally managed configurations are then shared with specific environments or workspaces, allowing Scalr to automatically pass the necessary authentication details to Terraform or OpenTofu runs for deploying and managing your infrastructure.
OIDC for Dynamic Cloud Provider Credentials: Scalr supports OIDC for obtaining dynamic, short-lived credentials from cloud providers such as AWS, Azure, and GCP. This method avoids the use of long-lived static credentials for Terraform and OpenTofu operations managed through the TACOS platform.
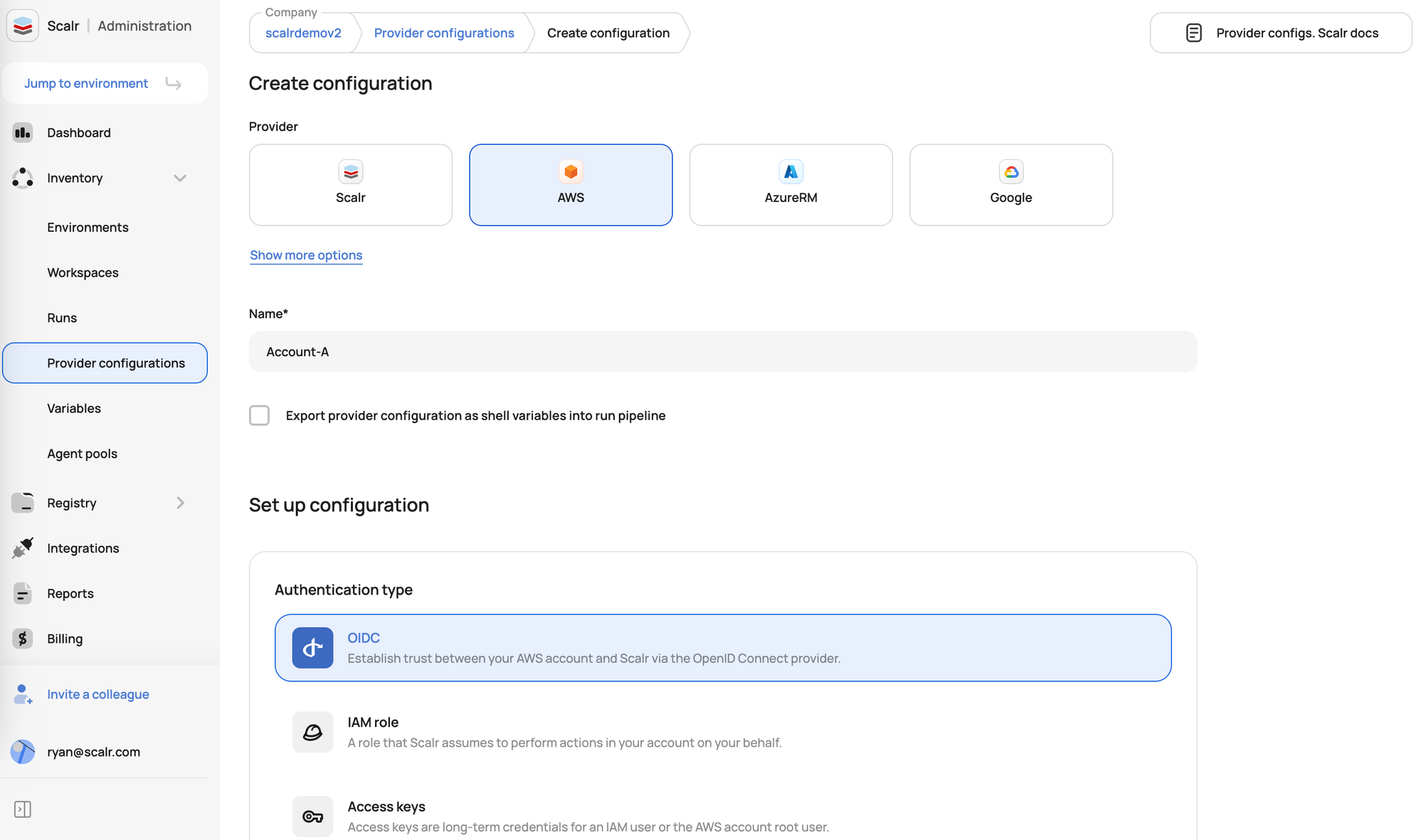
IaC Security Focused Tooling
Open Policy Agent Integration - Scalr integrates Open Policy Agent (OPA) to automatically check your Terraform and OpenTofu code against custom Rego policies during its workflow, before infrastructure changes are applied. This combination provides a way to consistently enforce security, compliance, and operational standards, offering centralized visibility and control over your Infrastructure as Code deployments.
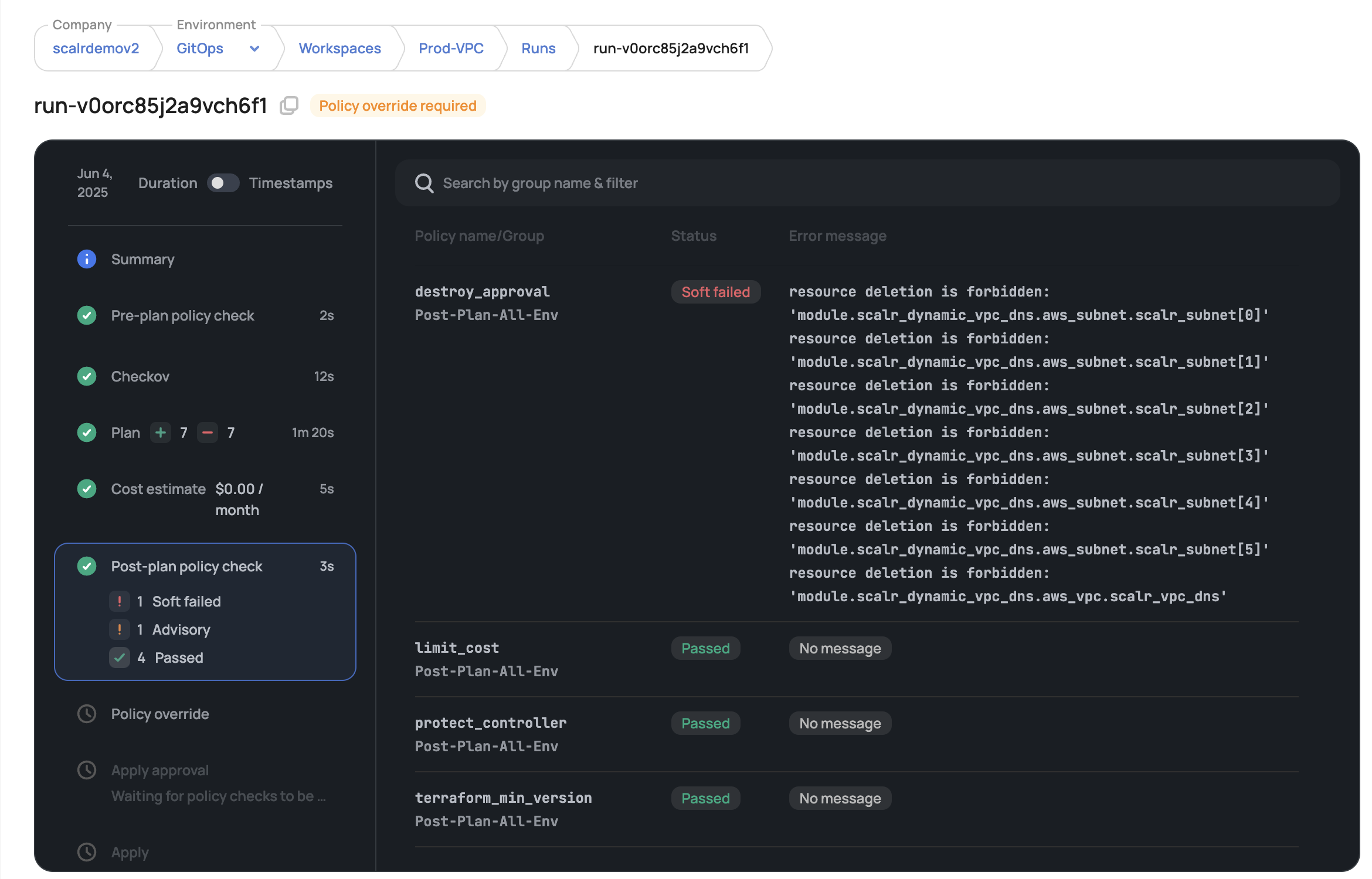
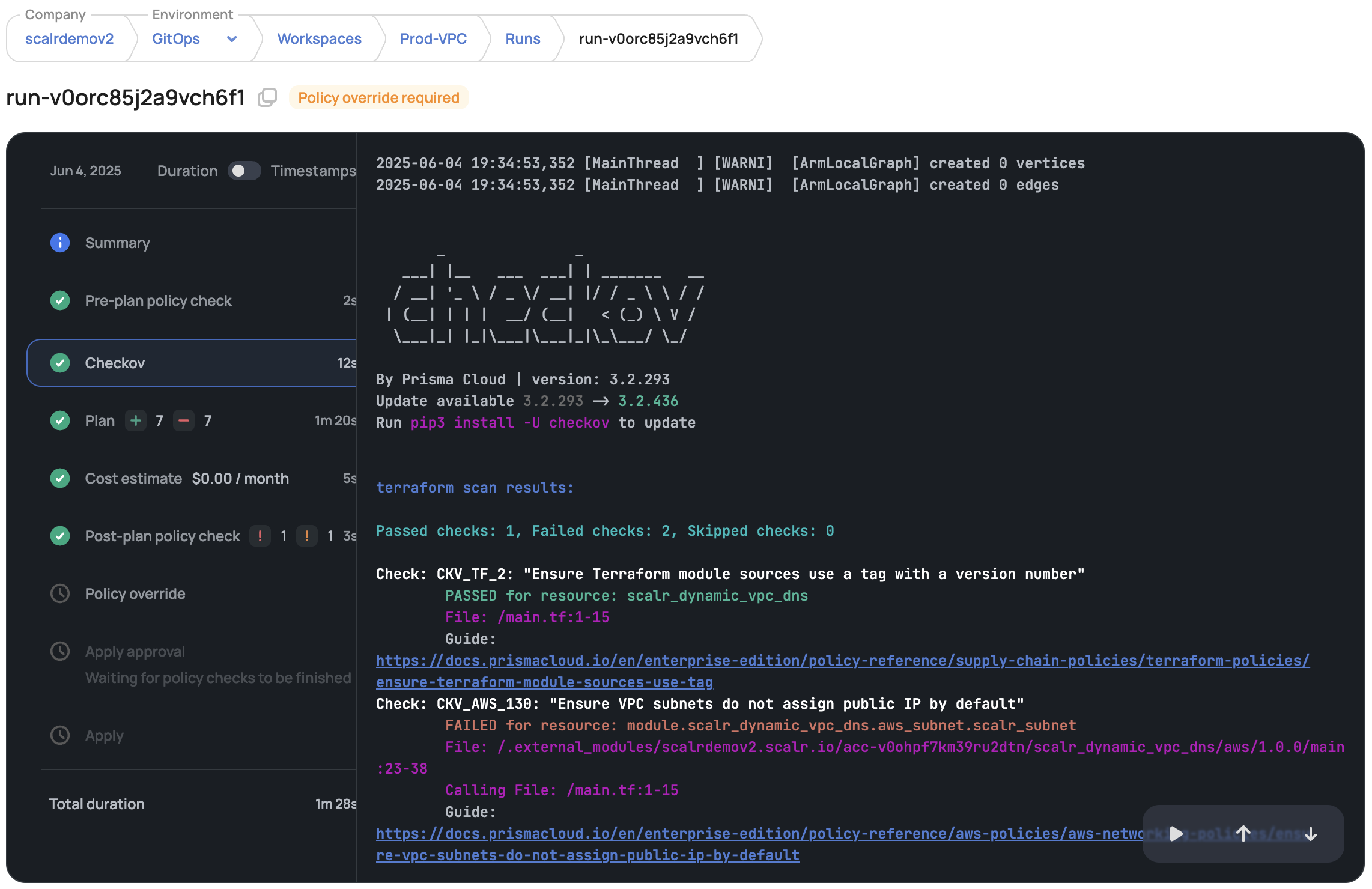
Checkov Integration for Security Scanning: Scalr integrates with Checkov, a static analysis tool for IaC. This integration allows for the scanning of Terraform and OpenTofu configurations for security misconfigurations and compliance issues as part of the TACOS pipeline.
Infrastructure & Data Security
Scalr provides features to protect IaC configurations and associated data within a TACOS workflow:
VCS Agents for Internal VCS Connectivity: For organizations with version control systems (VCS) hosted internally (e.g., self-hosted GitHub, GitLab, Bitbucket), Scalr offers VCS Agents. These agents establish a secure connection from Scalr to the internal VCS, allowing access to IaC code without exposing the VCS to the public internet.
Self-Hosted Agents for Controlled Execution Environments: Scalr allows the use of self-hosted agents. This enables organizations to run Terraform and OpenTofu operations within their own network infrastructure, providing control over the execution environment.
- Scalr-Managed Storage: When Scalr manages the backend for Terraform or OpenTofu state files, these files are encrypted at rest.
- Customer-Managed Storage: If an organization uses its own storage solution (e.g., AWS S3, Azure Blob Storage) as the backend, the encryption of the state file is managed by the security configurations of that customer-provided storage service, not directly by Scalr.
Secure Variable Management: Scalr provides a system for managing variables, including sensitive data such as API keys and passwords. These variables are stored encrypted and are intended for use in Terraform and OpenTofu configurations.
Reporting
Scalr offers several reporting features that significantly enhance security posture management for your Infrastructure as Code (IaC) deployments. These reports provide centralized visibility and actionable insights, helping you maintain compliance and identify potential risks across all your environments and workspaces. Here's how Scalr's reporting aids in security:
OPA Policy Violation Reporting
- Scalr integrates with Open Policy Agent (OPA) to enforce custom security and compliance policies on your Terraform and OpenTofu configurations.
- When a run violates an OPA policy, Scalr reports these violations. This includes details about which policy was violated, the resources involved, and why the violation occurred.
- This allows security teams to quickly identify non-compliant deployments and developers to understand and remediate issues before infrastructure is provisioned or modified.
- Scalr also offers "dry runs" or impact analysis for OPA policy changes, showing which existing workspaces would violate a new or modified policy before it's enforced. This helps prevent unexpected disruptions and allows for proactive remediation.
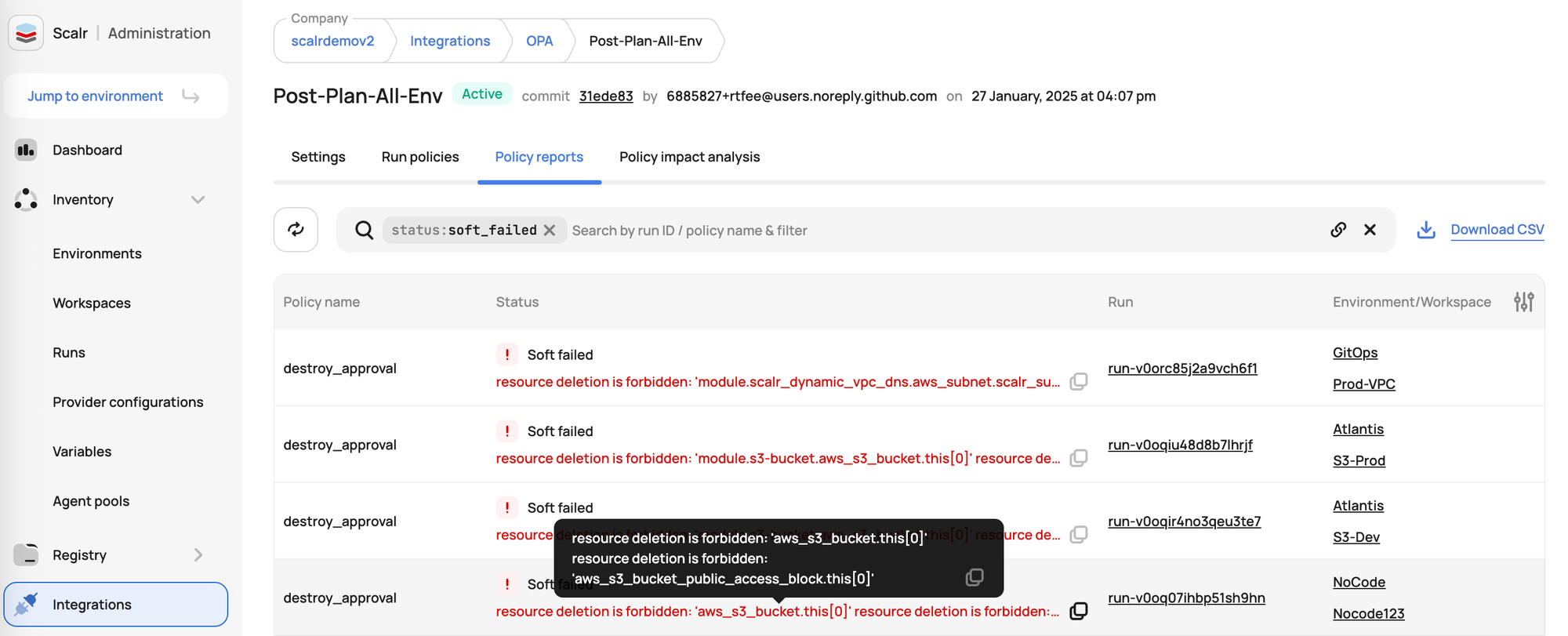
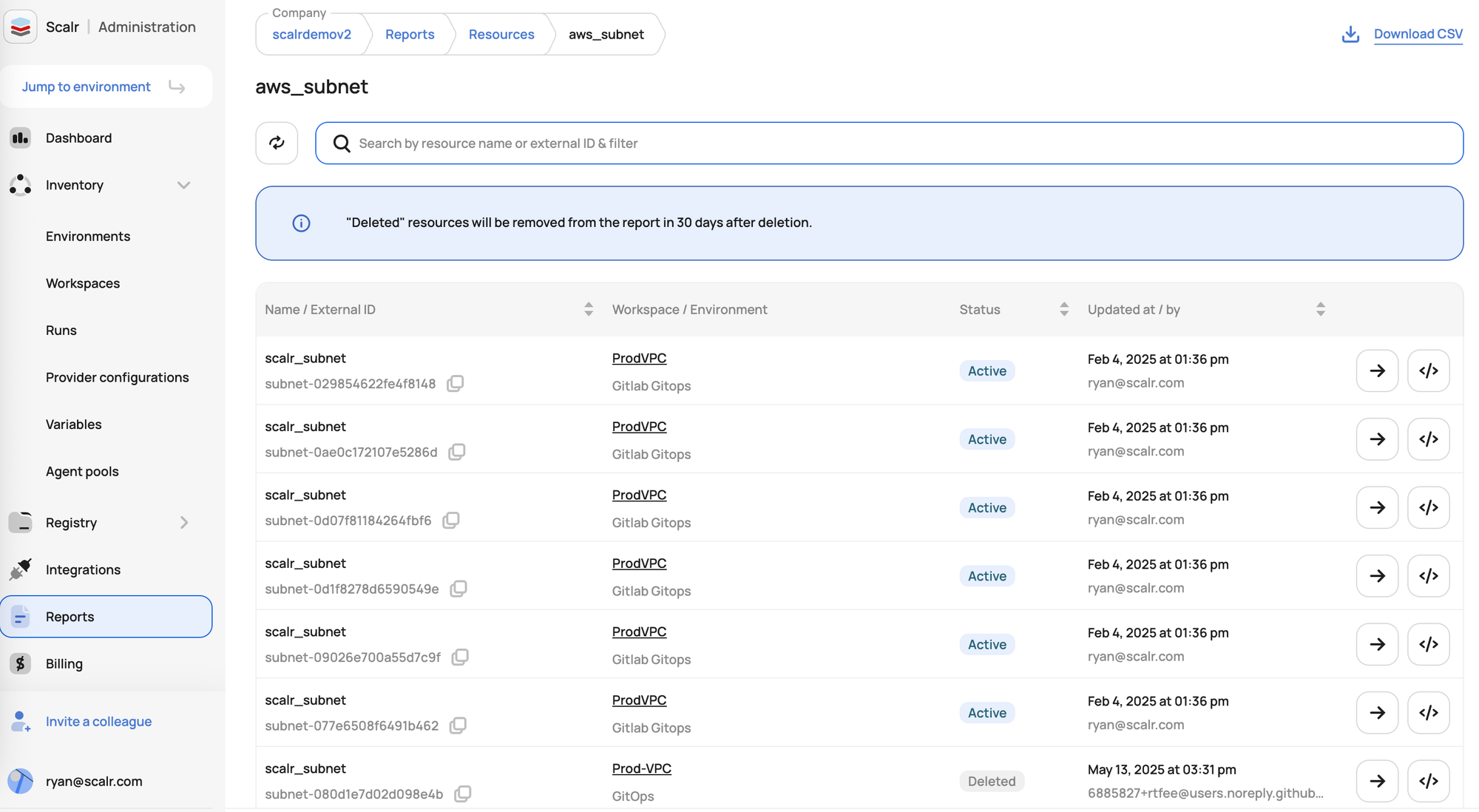
Resource and Configuration Tracking
- The Terraform & OpenTofu Resources report aggregates all resources across your state files into a single dashboard. This helps in identifying active and even recently deleted resources.
- For security, this means you can track the configuration of sensitive resources, audit who made changes, and identify potentially orphaned or unmanaged resources that could pose a risk.
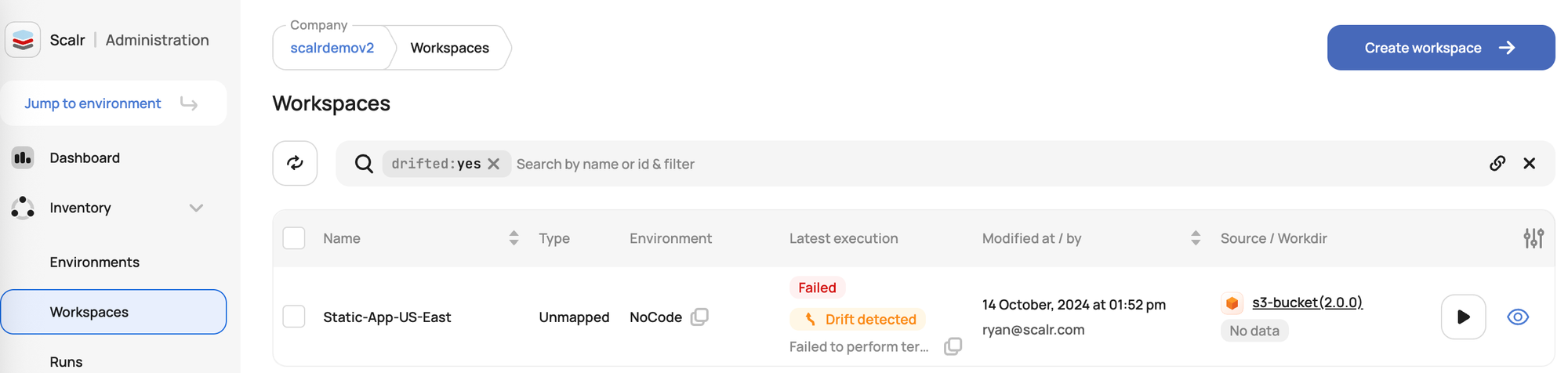
Drift Detection Reports
- Scalr provides drift detection capabilities, identifying discrepancies between the actual state of your infrastructure and its intended configuration in your IaC code.
- Drift can lead to security vulnerabilities or compliance violations if unauthorized or unmanaged changes occur.
- Reports on drifted workspaces, along with notifications, allow security teams and operators to quickly identify and address these deviations, ensuring the infrastructure remains in its desired, secure state.
Version Management Reports (Terraform/OpenTofu, Modules, Providers)
- Scalr reports on the versions of Terraform/OpenTofu, modules, and providers being used across all workspaces.
- From a security perspective, this is crucial for identifying and phasing out outdated components that may contain known vulnerabilities. It helps ensure that your infrastructure is built using approved and patched versions, reducing the attack surface.
- You can also identify if workspaces are pulling modules or providers from unapproved sources.
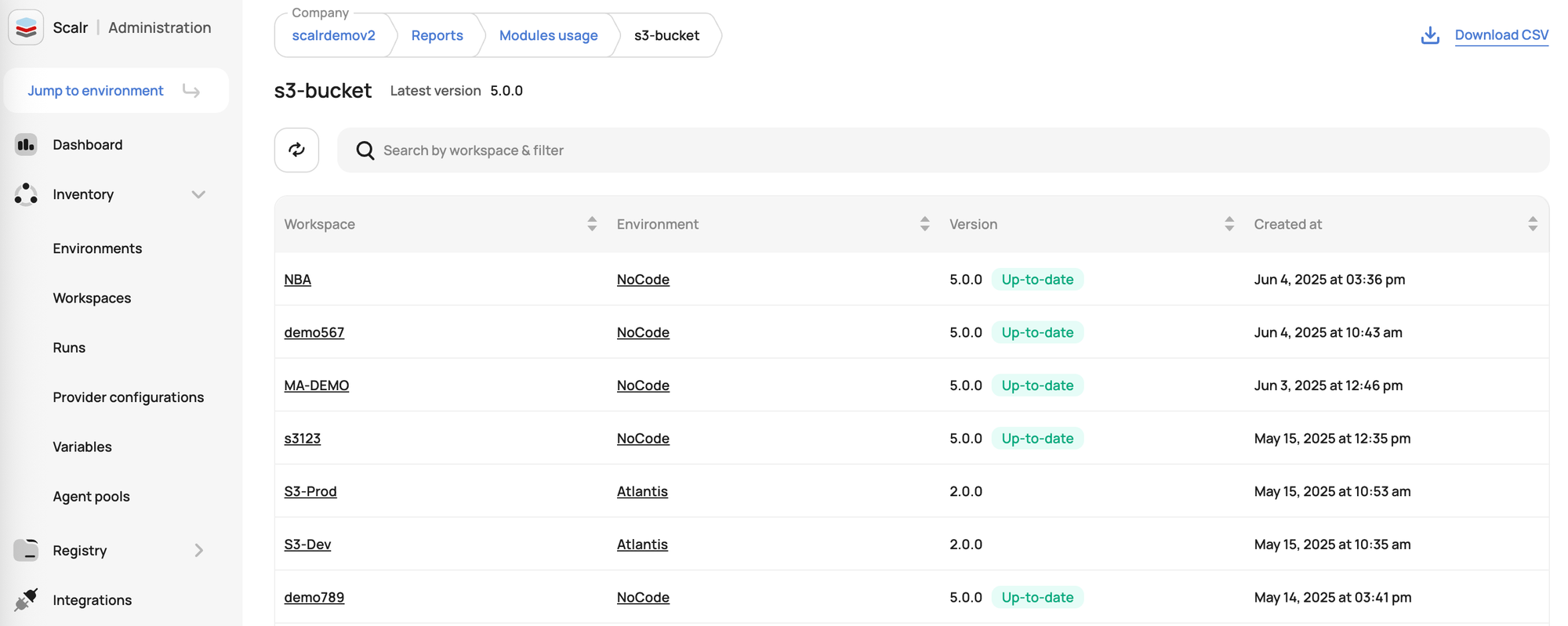
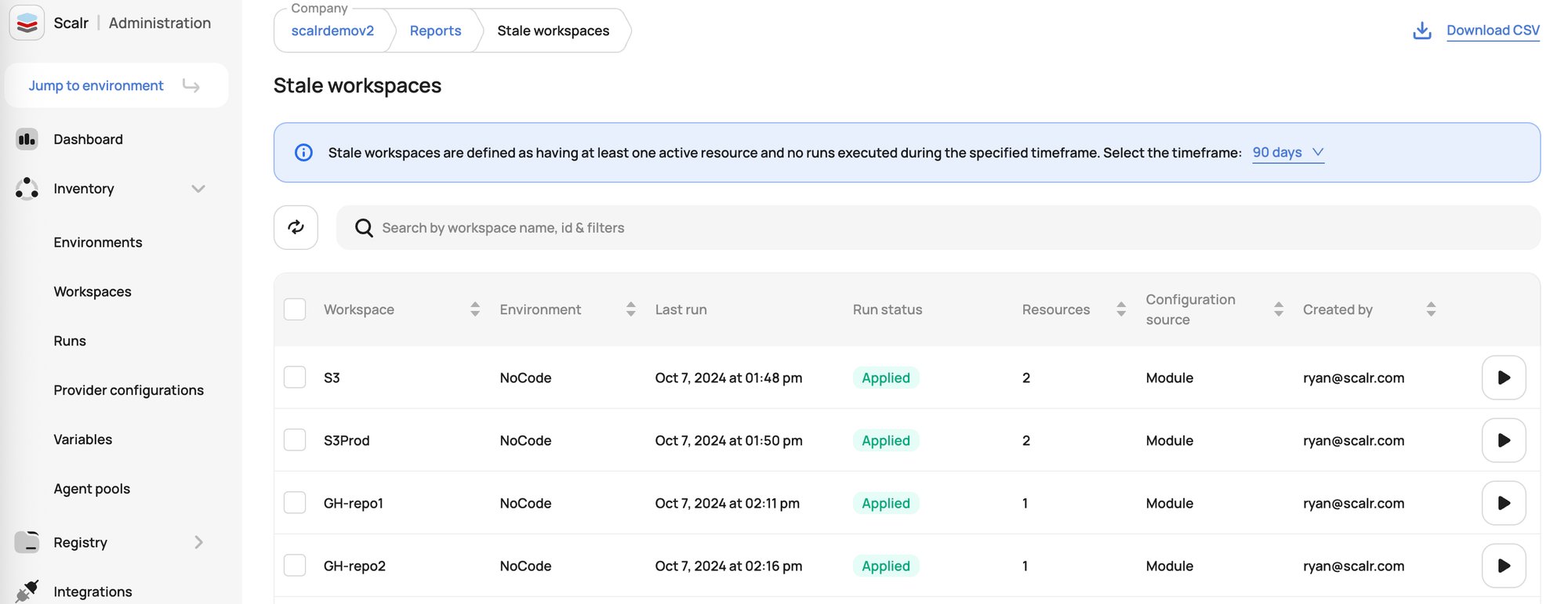
Stale Workspace Reports
- This report lists workspaces with active resources that haven't executed a run in a specified timeframe.
- Stale workspaces can pose security risks as their configurations might not be up-to-date with the latest security policies or patches. This report helps identify these potentially neglected environments so they can be reviewed and updated.
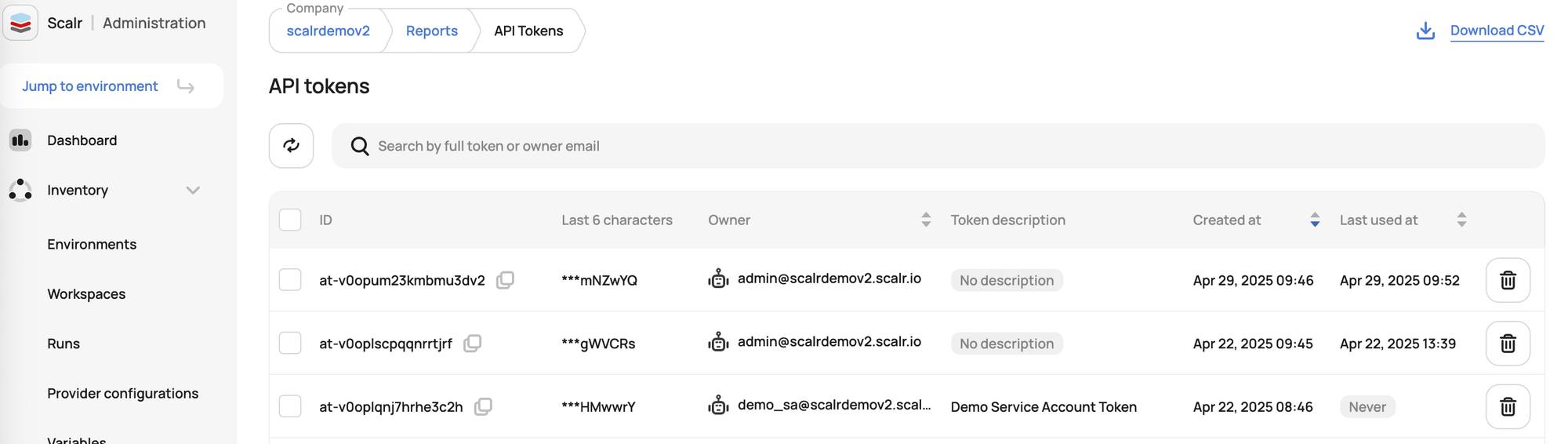
API Token Reports
- Administrators can identify API tokens that haven't been rotated or have never been used.
- Regular rotation of API tokens is a security best practice to protect against unauthorized access. This report helps enforce that practice.
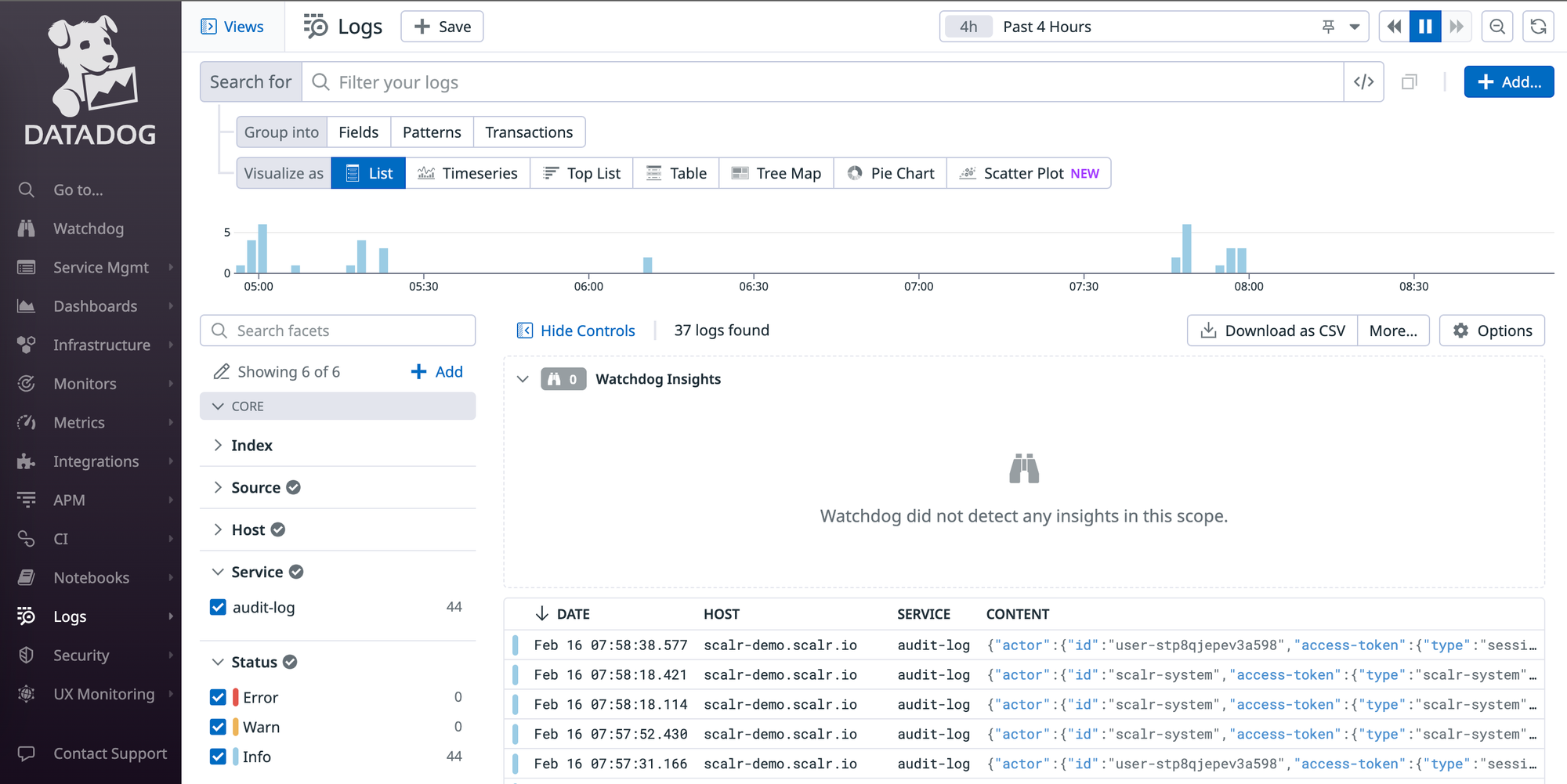
Audit Logs
While not a specific "report" in the same UI section, Scalr maintains audit logs that provide a detailed trail of activities within the platform. This is invaluable for security investigations, compliance audits, and understanding who did what, when. The audit logs are sent to Datadog of AWS EventBridge to be analyzed.
By consolidating this information, Scalr's reporting features allow organizations to move from a reactive to a more proactive security stance. They provide the necessary visibility to enforce security policies consistently, detect deviations quickly, and maintain a stronger, more auditable security posture for their cloud infrastructure managed by Terraform or OpenTofu.
Summary
Scalr's security features are designed to address common security considerations in managing Terraform and OpenTofu at scale through a TACOS platform, focusing on access control, credential management, and the protection of infrastructure code and state.

