Scalr support for IaC tools Terraform, OpenTofu, Terragrunt
Scalr now seamlessly supports Terraform, OpenTofu and Terragrunt, unifying remote state, policies and automation for easier multi-IaC management.
In this blog, we will review managing your Infrastructure as Code (IaC) when you're juggling Terraform, OpenTofu, or Terragrunt. We all know the power these tools bring, but scaling them across teams and projects can turn into a real headache pretty fast. That's where a platform like Scalr can make a difference, not by getting in your way, but by smoothing out the rough edges.
Scalr and Your IaC: Making Life Easier
The core idea behind Scalr is to provide a consistent operational framework around your chosen IaC tool. Think centralized state management, sensible access controls, and visibility into what's happening, without forcing you to completely change how you write your code.
Terraform with Scalr
Terraform is fantastic, but as soon as you're not a solo developer on a single project, things like state file management, concurrent runs, and ensuring everyone has the right permissions become non-trivial.
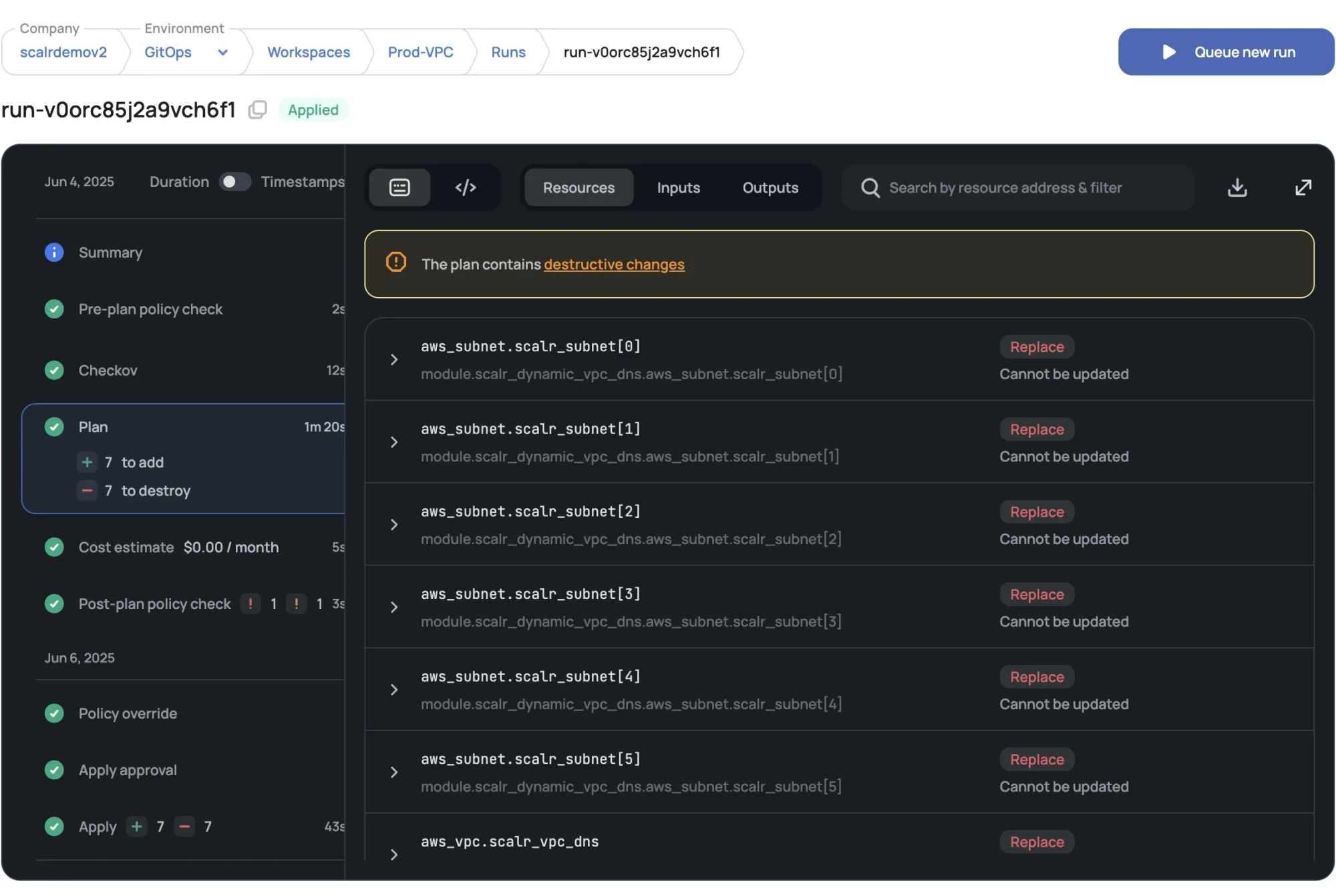
Pain Point: State File Chaos and Conflicts Remember the "who has the latest state file?" dance or accidentally stomping on someone else's apply? Scalr steps in by providing a remote backend for your Terraform state. This means no more S3 bucket policies to wrestle with for every new project or worrying about state locking.
A typical backend configuration in your Terraform code when using Scalr might look something like this:
Terraform
terraform {
backend "remote" {
hostname = "your-scalr-account.scalr.io"
organization = "your-organization-name"
workspaces {
name = "your-workspace-name"
}
}
}
Scalr handles the storage, encryption, and locking of that state file for you.
Pain Point: "It Works On My Machine" and Inconsistent Environments Scalr allows you to define workspaces that are linked directly to your VCS repositories (like GitHub, GitLab, etc.). You can map branches to workspaces, ensuring that a push to main triggers a run in your production workspace, while a push to a feature branch can deploy to a dev environment. This brings consistency. Variables, including sensitive ones, are managed within Scalr and injected at runtime, so no more .tfvars files with secrets floating around.
Success Indicator: Fewer "oops, I deployed to prod" moments. Faster, more reliable deployments because the environment configuration is managed centrally. You'll also see quicker onboarding for new team members as they don't need to configure a complex local setup.
Pain Point: Who Ran What, and Was it Allowed? Scalr provides Role-Based Access Control (RBAC) and integrates with Open Policy Agent (OPA). This means you can define who can plan, apply, or approve runs for specific workspaces. OPA integration lets you enforce custom policies on your Terraform code before an apply happens, catching potential issues early.
For example, you might have a policy that prevents deploying oversized VMs. If a terraform plan violates this, Scalr can flag it or even block the apply.
Success Indicator: Clear audit trails. Reduced risk of unauthorized changes. Compliance requirements are easier to meet because policies are enforced automatically.
OpenTofu: The Open Source Path with Scalr
For those moving to or starting with OpenTofu, the good news is that Scalr's support is seamless because OpenTofu maintains compatibility with Terraform. The pain points and how Scalr addresses them are largely the same.
Pain Point: Ensuring a Smooth Transition and Future-Proofing If you're migrating from Terraform to OpenTofu, Scalr can act as a consistent management layer. You point your OpenTofu configurations to Scalr just like you would with Terraform. Scalr's execution environment can run your tofu commands.
Your backend configuration for OpenTofu would be identical to the Terraform example:
Terraform
terraform { // Yes, it's still 'terraform' block for OpenTofu compatibility
backend "remote" {
hostname = "your-scalr-account.scalr.io"
organization = "your-organization-name"
workspaces {
name = "your-opentofu-workspace"
}
}
}
Pain Point: Parity in Tooling and Collaboration Scalr offers the same set of features for OpenTofu as it does for Terraform: version control integration, workspace management, RBAC, OPA policy enforcement, and centralized run viewing. This means your team doesn't have to learn a new set of operational tools if they switch to OpenTofu.
Success Indicator: Teams can adopt OpenTofu without disrupting their existing IaC workflows managed by Scalr. Consistent policy enforcement and collaboration features work out-of-the-box.
Getting a Grip on Terragrunt with Scalr
Terragrunt is great for keeping your Terraform configurations DRY (Don't Repeat Yourself) and managing multiple environments or modules. Scalr complements Terragrunt by providing the execution and governance layer.
Pain Point: Orchestrating Terragrunt Runs at Scale While Terragrunt helps organize your code, you still need a way to trigger runs, manage approvals, and see the output across many Terragrunt modules or stacks. Scalr can trigger your Terragrunt commands (terragrunt apply-all, terragrunt plan-all) within its managed execution environment.
You would typically structure your repository with Terragrunt HCL files, and Scalr workspaces would point to the directories containing these files. Scalr then executes Terragrunt, which in turn calls Terraform/OpenTofu.
A simplified Terragrunt setup might look like this in your terragrunt.hcl:
Terraform
remote_state {
backend = "remote"
config = {
hostname = "your-scalr-account.scalr.io"
organization = "your-organization-name"
workspaces = {
// Terragrunt can dynamically set this or you can configure it
name = "terragrunt-${path_relative_to_include()}"
}
}
}
inputs = {
// Your common variables
}
Scalr becomes the unified place to see the status of these apply-all or plan-all operations.
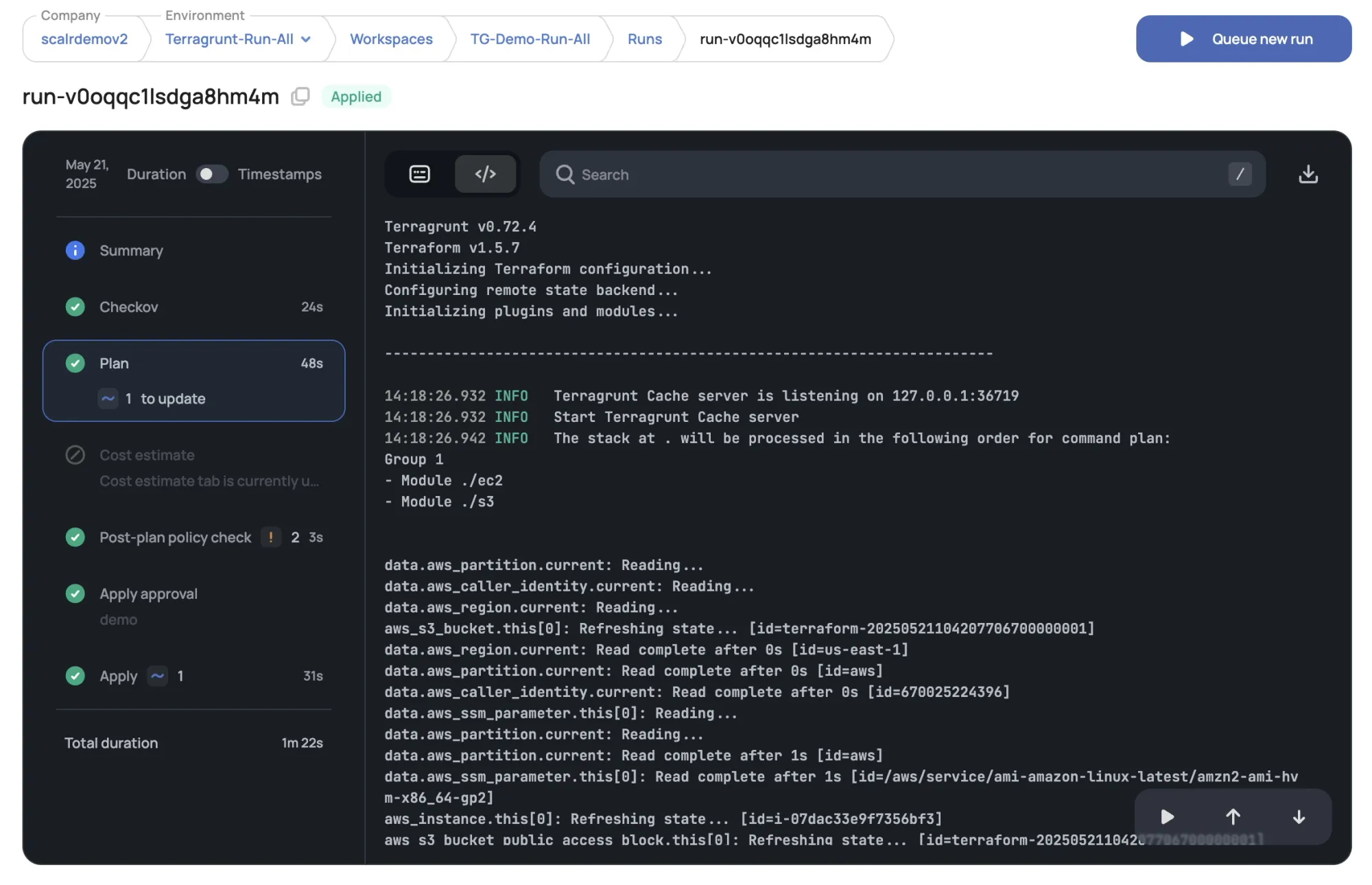
Pain Point: Environment Promotion and Consistency Terragrunt is often used to manage dependencies between modules and promote changes through environments (dev -> staging -> prod). Scalr’s VCS integration helps here. For example, merging a feature branch into develop could trigger Terragrunt runs for your dev environment workspaces in Scalr. Merging develop into main could then trigger runs for staging or production.
Success Indicator: Clearer visibility into complex Terragrunt deployments. Easier promotion of configurations across environments with predictable outcomes. The same RBAC and OPA policies apply, ensuring governance even with Terragrunt's layered approach.
Pain Point: Debugging and Visibility into Terragrunt Runs Debugging a terragrunt apply-all failure can sometimes mean digging through a lot of console output. Scalr provides a centralized view of all the logs from your Terragrunt runs, making it easier to pinpoint where things went wrong within a specific module.
Success Indicator: Reduced time spent debugging Terragrunt deployments. Developers can quickly identify which part of a multi-module deployment failed and why.
In essence, Scalr aims to take away the operational burdens of using Terraform, OpenTofu, or Terragrunt at scale, letting you focus on writing good IaC. It’s about providing that governance, visibility, and collaboration layer without making you throw out the tools you already know and like. Scalr enhances infrastructure as code (IaC) workflows by providing a unified platform for Terraform, OpenTofu, and Terragrunt. It centralizes state management, simplifies collaboration, and integrates policy enforcement and cost estimation across these tools.
By offering robust support for Terraform, OpenTofu, and Terragrunt, Scalr aims to unify your IaC practices, making them more secure, collaborative, and efficient. It tackles the common operational hurdles, letting you focus more on defining your infrastructure and less on the surrounding mechanics.

